3.1 Introduce Memory Hierarchy
Memory is a part of a computer system that is used to store data or instruction temporarily and permanently.
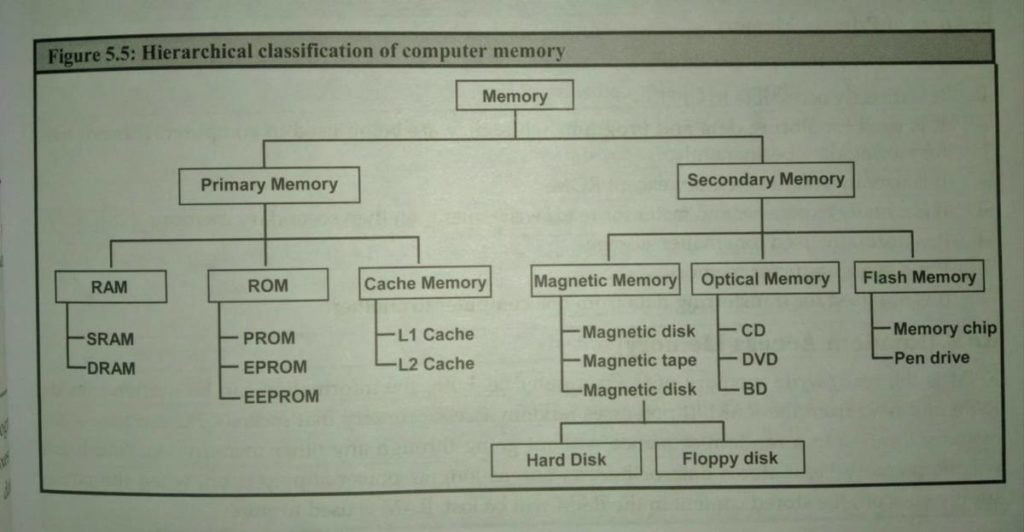
Memory is primarily of two types:
- Primary Memory
- Secondary Memory
1. Primary Memory
It is also known as system memory. It holds data and instructions for processing. It holds data after it is processed waiting to be sent to an output device.
- RAM: random access memory is the read and writes memory. It is a volatile memory. It is the type of memory that can be accessed from any random location without going through any other memory location.
- SRAM: Static Random Access Memory stored data and programs. As long as the computer is in on state. It is expensive but faster than DRAM memory.
- DRAM: dynamic random-access memory is a type of memory that will be too after a few milliseconds, even if the computer is in an ON state.
- ROM: Read Only Memory is a type of memory used only for read operation. It does have write capabilities. The information stored in it is permanent.
- PROM: Programable Read Only Memory is a programmable memory. It is once programmable i.e.; the user can write data in a PROM only. It is permanent.
- EPROM: Erasable Programmable Read-Only Memory is a type of Memory in which data is stored and can be exposing it to ultraviolet rays.
- EEPROM: Electrical Erasable Programmable Read-Only Memory is a type of Memory that can be used to store data and can be erased Electrically on a byte-by-byte basis.
- Cache Memory: Cache Memory is a high-speed memory that is placed between CPU and RAM. It is used in CPU so that CPU doesn’t have to wait for the data to be delivered
2. Secondary Memory:
The secondary storage devices which are built into the computer or connected to the computer are known as a secondary memory of the computer. It is also known as external memory or auxiliary storage.
- Magnetic Memory: Floppy Disk, hard disk, and magnetic tape (reel) use similar technology for reading and writing data. The surface of these devices is coated with magnetically sensitive material such as iron oxide which reacts to the magnetic field. The orientation of a magnetic field is used to represent data.
- Magnetic Disk: A magnetic Disk is a type of secondary memory that is a flat disc covered with a magnetic coating to hold information. It is used to store various programs and files. The polarized information in one direction is represented by 1, and vice versa. The direction is indicated by 0.
- Hard Disk: The hard disk is also known as a hard drive. It is a rigid magnetic disc that stores data permanently, as it is a non-volatile storage device. The hard disk is located within a drive unit on the computer’s motherboard and comprises one or more platters packed in an air-sealed casing. The data is written on the platters by moving a magnetic head over the platters as they spin.
- Floppy Disk: A floppy disk is a type of storage media that reads data storage information, also known as a floppy diskette, floppy, or floppy disk that is used to store electronic data, like a computer file. It was extremely expensive as it was one of the first types of hardware storage created in 1967 by IBM, which could read/write a portable device.
- Magnetic Tape: The magnetic tape contains a thin plastic ribbon that is used for storing data. It is a sequential access memory. So, the data read/write speed is slower. It is mainly used for data backups.
- Optical Memory: Optical memory is an electronic storage medium that uses a laser beam to store and retrieve data. The optical memory is a round disk with a shiny surface on which data is imprinted by means of a laser beam. Thus, optical technology was first used to represent analog sound signals into digital form.
- CD: It is 4.75 in diameter, which is a flat, round, portable storage medium used to record, store, and playback audio, video, and other data.
- DVD: DVD stands for Digital Versatile Disc. It is commonly known as Digital Video Disc. It is a digital optical disc storage format used to store high-capacity data like high-quality videos and movies. It is also used to store the operating systems.
- BD: BD is the name of the new generation optical disk. It is developed to enable recording, rewriting, and playback of high-definition video (HD), as well as storing a large amount of data. This disk offers more than five times the storage capacity of present DVDs.
- Flash Memory: Flash memory is a non-volatile memory chip used for storage and for transferring data between a personal computer (PC) and digital devices. It has the ability to be electronically reprogrammed and erased. It is often found in USB flash drives, MP3 players, digital cameras, and solid-state drives.
- Memory Chip: A memory card is a type of storage device that is used to store videos, photos, or other data files. It offers a volatile and non-volatile medium to store data from the inserted device. It is also referred to as a flash memory.
- Pen drive: A USB flash drive is a device used for data storage that includes a flash memory and an integrated Universal Serial Bus (USB) interface. Most USB flash drives are removable and rewritable. Physically, they are small, durable, and reliable. The larger their storage space, the faster they tend to operate.
3.2 Explain Memory Function
- Allocate and de-allocate memory before and after process execution.
- To keep track of used memory space by processes.
- To minimize fragmentation issues.
- To proper utilization of main memory.
- To maintain data integrity while executing of process.
3.3 Describe Mono programming model and Multiprogramming model
* Monoprogramming without Swapping or Paging:
The simplest possible memory management scheme is to run just one program at a time, sharing the memory between that program and the operating system.
When the system is organized in this way, only one process at a time can be running. As soon as the user types a command, the operating system copies the requested program from disk to memory and executes it. When the process finishes, the operating system displays a prompt character and waits for a new command. When it receives the command, it loads a new program into memory, overwriting the first one.
* Multiprogramming with Fixed Partitions:
Except on simple embedded systems, monoprogramming is hardly used anymore. Most modern systems allow multiple processes to run at the same time. Having multiple processes running at once means that when one process is blocked waiting for I/O to finish, another one can use the CPU. Thus, multiprogramming increases CPU utilization. Network servers always have the ability to run multiple processes (for different clients) at the same time, but most client (i.e., desktop) machines also have this ability nowadays.
3.4 Elaborate Sharing and protection.
* Memory Protection
Protecting the operating system from user processes and protecting user processes from one another. We can provide this protection by using a relocation register, with a limit register.
When the CPU scheduler selects a process for execution, the dispatcher loads the relocation and limit registers with the correct values as part of the context switch. Because every address generated by the CPU is checked against these registers, we can protect both the operating system and the other users’ programs and data from being modified by this running process.
* Memory Sharing
Shared memory is a memory that may be simultaneously accessed by multiple programs with an intent to provide communication among them or avoid redundant copies. Shared memory is an efficient means of passing data between programs. Depending on the context, programs may run on a single processor or on multiple separate processors. Shared memory refers to a (typically large) block of random-access memory (RAM) that can be accessed by several different central processing units (CPUs) in a multiprocessor computer system. A shared memory system is relatively easy to program since all processors share a single view of data and the communication between processors can be as fast as memory accesses to the same location.
3.5 Describe Static and dynamic partition
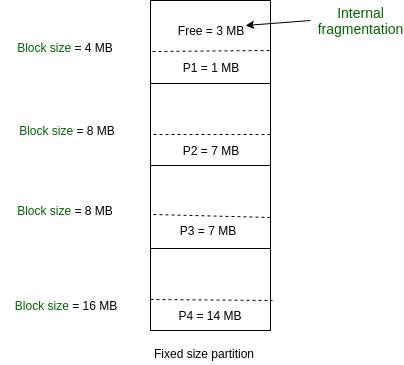
* Static Partitioning (Fixed Partitioning):
This is the oldest and simplest technique used to put more than one process in the main memory. In this partitioning, the number of partitions (non-overlapping) in RAM is fixed but the size of each partition may or may not be the same. As it is a contiguous allocation, hence no spanning is allowed. Here partitions are made before execution or during system configure.
Advantages of Static Partitioning
- Easy to implement
- Little OS overhead
Disadvantages of Static Partitioning
- Limit process size
- Limitation on Degree of Multiprogramming
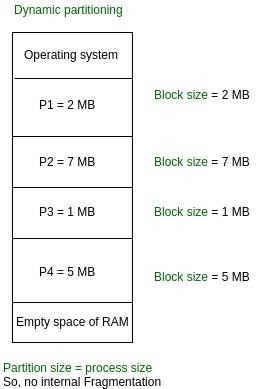
# Dynamic Partitioning (Variable Partitioning):
It is a part of the Contiguous allocation technique. It is used to alleviate the problem faced by Fixed Partitioning. In contrast with fixed partitioning, partitions are not made before the execution or during system configure. Various features associated with variable Partitioning-
- Initially RAM is empty and partitions are made during the run-time according to process’s need instead of partitioning during system configure.
- The size of partition will be equal to incoming process.
- The partition size varies according to the need of the process so that the internal fragmentation can be avoided to ensure efficient utilization of RAM.
- Number of partitions in RAM is not fixed and depends on the number of incoming process and Main Memory’s size.
Advantages of Fixed Partitioning
- No Internal Fragmentation
- No restriction on Degree of Multiprogramming
Disadvantages of Fixed Partitioning
- Difficult Implementation
- External Fragmentation
3.6 Explain Internal and External Fragmentation
* Fragmentation
As processes are loaded and removed from memory, the free memory space is broken into little pieces. It happens after sometimes that processes cannot be allocated to memory blocks considering their small size and memory blocks remain unused. This problem is known as Fragmentation.
- External fragmentation: Total memory space is enough to satisfy a request or to reside a process in it, but it is not contiguous, so it cannot be used.
- Internal fragmentation: The memory block assigned to the process is bigger. Some portion of memory is left unused, as it cannot be used by another process.
3.7 Illustrate the concept of Virtual Memory and Paging
* Virtual Memory
Virtual Memory is a storage allocation scheme in which secondary memory can be addressed as though it were part of the main memory. The addresses a program may use to reference memory are distinguished from the addresses the memory system uses to identify physical storage sites, and program-generated addresses are translated automatically to the corresponding machine addresses.
The size of virtual storage is limited by the addressing scheme of the computer system and the amount of secondary memory is available not by the actual number of the main storage locations.
It is a technique that is implemented using both hardware and software. It maps memory addresses used by a program, called virtual addresses, into physical addresses in computer memory.
All memory references within a process are logical addresses that are dynamically translated into physical addresses at run time. This means that a process can be swapped in and out of the main memory such that it occupies different places in the main memory at different times during the course of execution.
A process may be broken into a number of pieces and these pieces need not be continuously located in the main memory during execution. The combination of dynamic run-time address translation and use of page or segment table permits this.
* Paging
A computer can address more memory than the amount physically installed on the system. This extra memory is actually called virtual memory and it is a section of a hard that’s set up to emulate the computer’s RAM. The paging technique plays an important role in implementing virtual memory.
Paging is a memory management technique in which process address space is broken into blocks of the same size called pages (size is the power of 2, between 512 bytes and 8192 bytes). The size of the process is measured in the number of pages.
Similarly, main memory is divided into small fixed-sized blocks of (physical) memory called frames and the size of a frame is kept the same as that of a page to have optimum utilization of the main memory and to avoid external fragmentation.

I’ve read several good stuff here. Definitely worth bookmarking for revisiting. I surprise how much effort you put to create such a great informative website.
Enjoyed looking at this, very good stuff, regards. “All of our dreams can come true — if we have the courage to pursue them.” by Walt Disney.
I enjoy what you guys are up too. This sort of clever work and coverage! Keep up the wonderful works guys I’ve added you guys to blogroll.
When I originally commented I clicked the -Notify me when new comments are added- checkbox and now each time a comment is added I get four emails with the same comment. Is there any way you can remove me from that service? Thanks!
Wonderful web site. A lot of helpful info here. I’m sending it to some friends ans also sharing in delicious. And naturally, thank you to your effort!
I’ve recently started a site, the information you provide on this site has helped me greatly. Thanks for all of your time & work.
I as well conceive thus, perfectly pent post! .
Thank you for the support!
Well done! Thank you so much for the notes